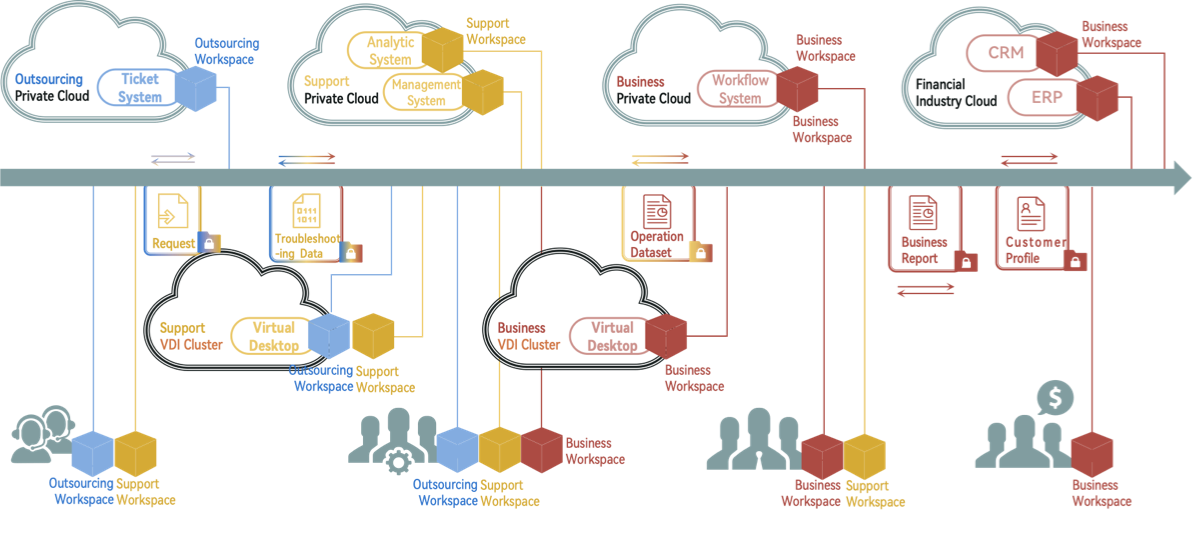
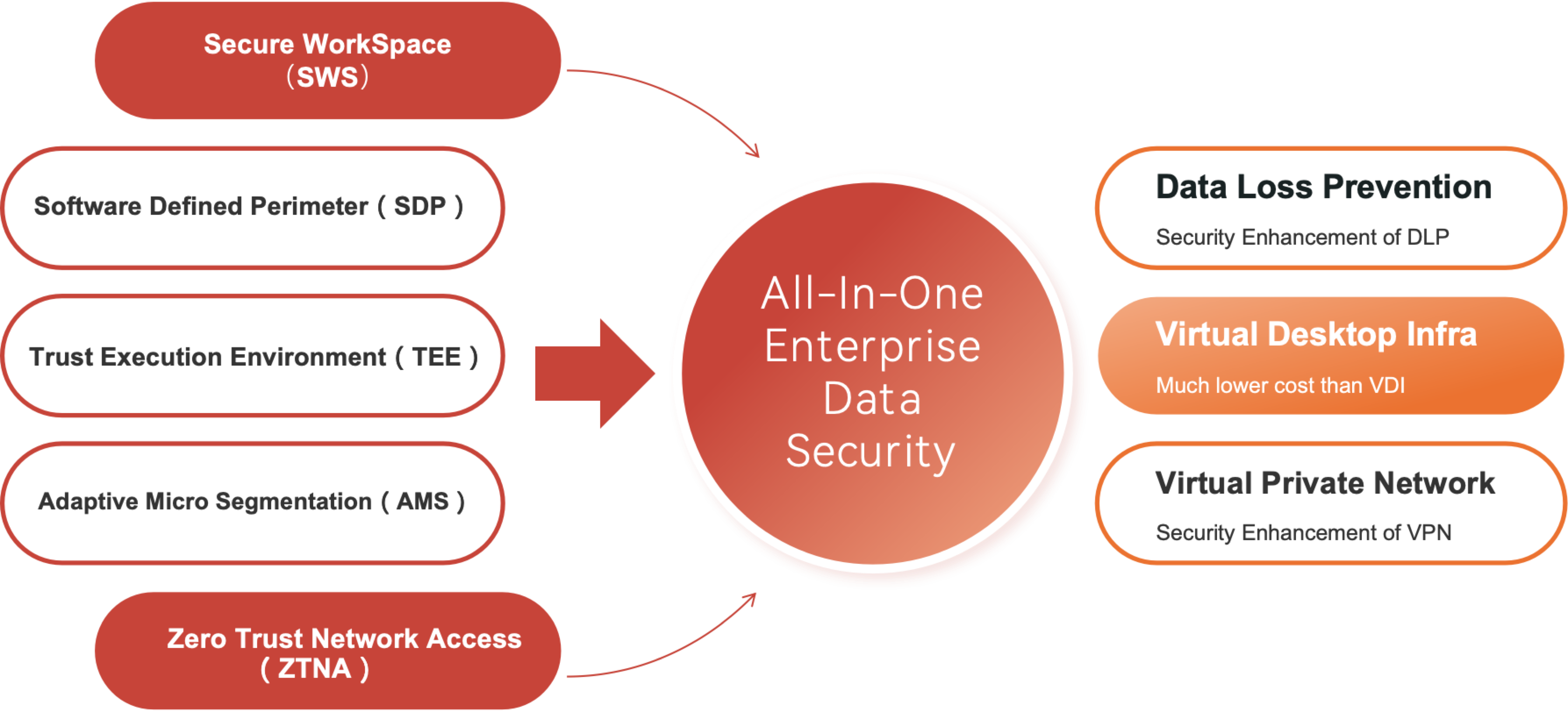
Financial Industry
Key Requirements:
- - Developer & Operator Environment Isolation to Prevent Unauthorized Access
- - Virtual Desktop Alternative for Low-Cost Security Infrastructure
- - Provide a Cross-organizational Collaboration Security Data Sharing Channel
- - Call Center & Outsourcing Protect Privacy and Confidential Business Information When Staff Turnover
Key Solutions:
- - By leveraging software-defined secure workspace technology, it is possible to effectively isolate the environments that developers, testers, and business operations personnel can access. This achieves 'three-network isolation,' preventing network connectivity risks caused by temporary authorizations and delays in revoking permissions.
- - Adopt a Secure Workspace (SWS) based on local lightweight virtualization to replace high-cost VDI for internal business access and data isolation, preventing sensitive internal data from leaking through local devices.
Crypto Exchange Industry

Key Requirements:
- - Prevent Ransomware from Locking and Breaching data on Desktop and Servers
- - Virtual Desktop Alternative for Low-Cost Security Infrastructure
- - Prevent Key Data Asset from Stolen by Insider and Phishing Attack
- - VPN Alternative for Remote Accessing and Enhance the Data Security Capability of Remote Working Infrastructure
- - Provide a Cross-organizational Collaboration Security Data Sharing Channel
- - Data and business analysis Protection for BI Team
Key Solutions:
- - Proactive Defense Mechanisms:
Implement deep data isolation based on trusted computing and kernel-level sandboxing technologies to ensure that sensitive information is 100% protected against data leakage. Leveraging proactive defense mechanisms, accurately identify risks and effectively block threats before they materialize, such as ransomware attacks, phishing attempts, and other malicious activities. - - Trusted Computing Technologies:
Ensuring that all hardware and software components are verified as trustworthy and operate within a secure environment. - - Security Sandbox:
Isolating critical operations and data within a protected environment where any suspicious activity can be contained and analyzed without affecting the rest of the system. - - Zero Trust architecture:
Achieve a secure environment for BYOD (Bring Your Own Device) and remote employee work
Hi-Tech Manufacturing Industry
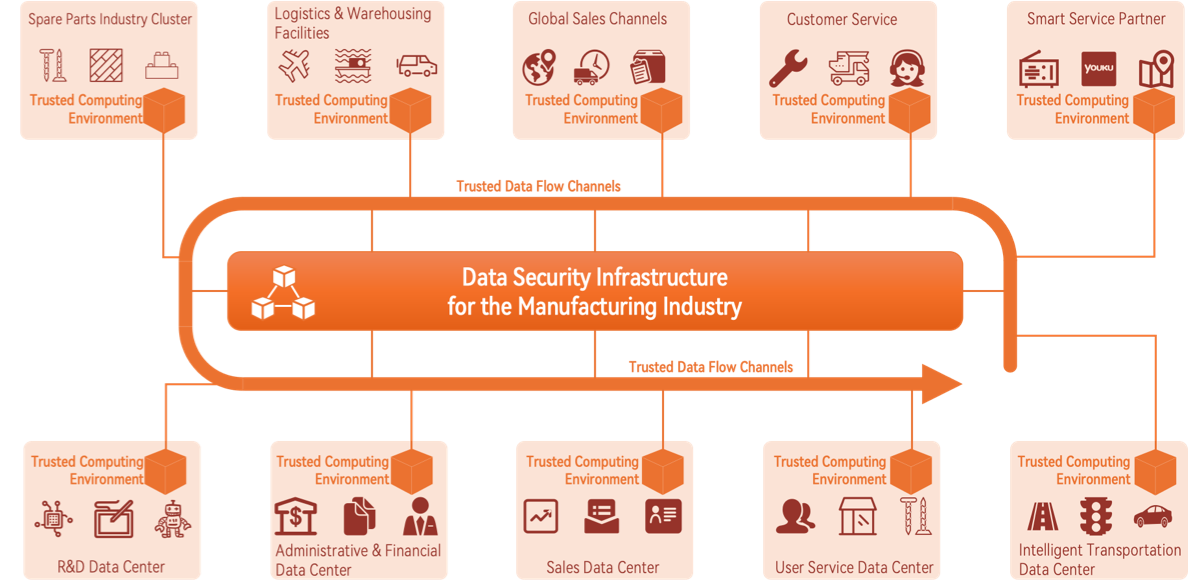
Key Requirements:
- R&D and Design-oriented Enterprises:
- Prevent Core Intellectual Property Breaching: Chip Design Layout, Core Design Documents, Confidential Agreements etc. - - Focusing on large-scale design and development software such as CAD (Computer-Aided Design), CATIA, SolidWorks, and EDA (Electronic Design Automation), the goal is to create a smooth, secure, and compliant office experience.
- Production and Manufacturing Enterprises:
- Focusing on BOM (Bill of Materials), MES (Manufacturing Execution System), ERP (Enterprise Resource Planning), and CRM (Customer Relationship Management), ensuring data security throughout the full process of digital production and operations involves implementing robust measures to protect critical business information across these integrated systems. - - To establish a secure data sharing platform for the upstream and downstream of the manufacturing supply chain, ensuring the security of the core data assets of the principal party
Key Solutions:
- - Implement a comprehensive data protection solution for the entire lifecycle of data in the design and manufacturing processes of the production industry, ensuring the security of core digital assets.
- - Instead of using file encryption and decryption software, adopt a secure workspace solution to achieve 100% precise isolation of core data assets. This approach avoids file corruption that can occur during the encryption and decryption process during file transfers.
- - Provide an efficient and secure file sharing channel, enabling internal employees and upstream and downstream supply chain partners to share data more securely and conveniently.
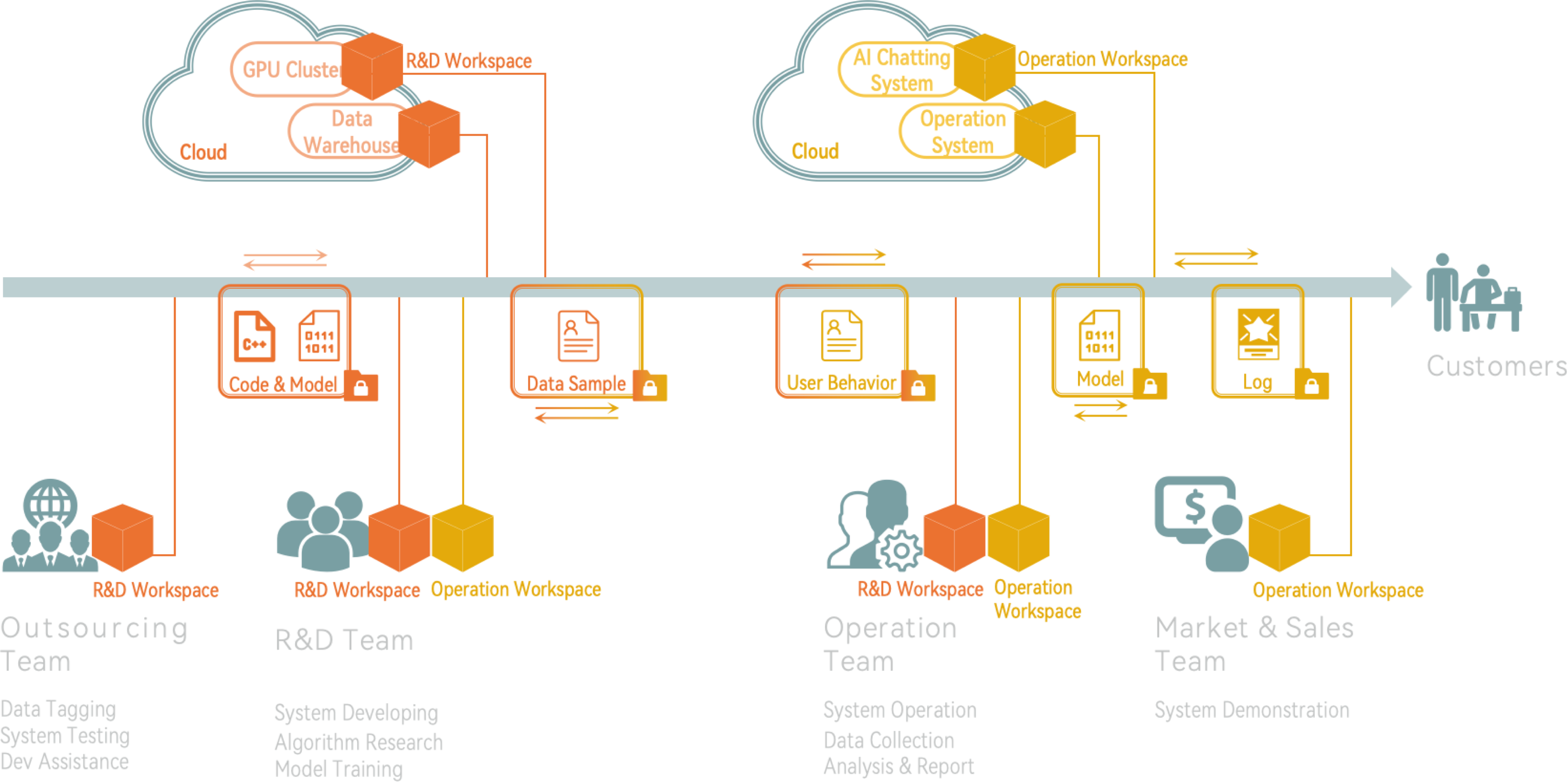
AI Industry
Key Requirements:
- - AI large model companies need to invest substantial resources in model training, and the trained weight data are extremely valuable. It is necessary to protect these core weight assets cautiously to prevent any leakage of confidential information
- - Small and medium-sized AI enterprises often cannot afford the expensive hardware required for model training tasks and therefore need to rent shared computing services. However, there is concern about the security of core training data during the rental process, as it may not be possible to fully guarantee the safety of this data when using such services.
Key Solutions:
- - Enable AI Companies to Build System over Public Cloud
- - Provide a secure and isolated environment to access public AI services such as ChatGpt, DeepSeek, Gemini, Midjourney, etc., ensuring that core sensitive enterprise data is not leaked to these public AI services.
Consumer Internet Industry
Key Requirements:
- Game Producer:
- Protect the security of game development assets, such as backend code, core intellectual property (IP) assets, art assets, design concepts, and other creative materials. Avoid private realms. - Internet Call Center & Outsourcing:
- Protect Privacy and Confidential Business Information When Staff Turnover
Key Solutions:
- - By ensuring that all game development work—ranging from entrepreneurship and design to R&D, art, operations, and release—is conducted within a secure workspace, you can effectively prevent internal theft of game development data. This reduces the risk of private servers becoming prevalent and helps maintain the integrity and security of your game's intellectual property.
- - Apply Zero Trust Architecture to enhance working experience and safety for Remote Working, replace VPN for Data Security and Minimize the exposure of internal website on Internet
Telecom operator Industry
Key Requirements:
- - Provide secure remote access capabilities based on Zero Trust technology for a large number of business outlets operated by telecom carriers, preventing internal business websites from being directly exposed to the internet.
Key Solutions:
- - Single Package Authentication(SPA):
Achieve network invisibility for internet-exposed business systems, avoiding exposure of detectable TCP ports, and implement separation between the control plane and data plane. - - Multi-Factor Authentication (MFA):
Require MFA for all access attempts, adding an extra layer of security beyond just usernames and passwords. This ensures that even if credentials are compromised, unauthorized access is still unlikely. - - Micro-Segmentation(MS):
Use micro-segmentation to divide the network into smaller, isolated segments. This limits lateral movement within the network and reduces the risk of breaches spreading across different parts of the system.
Government Industry
Key Requirements:
- - Ensure effective isolation between government intranets and the internet, ensuring that endpoints do not become connection points that compromise network isolation.
Key Solutions:
- - Deploy a Zero Trust Secure Workspace (SWS) on government terminals to effectively isolate applications accessing the government network. These applications will be restricted to accessing only the government network and will be unable to access the internet. Downloaded data can only be saved within the secure workspace, where it is encrypted upon landing. Even if the PC's hard drive is removed, sensitive government data cannot be stolen.