Products
Dataillusion SWS™ (Secure Work Space)
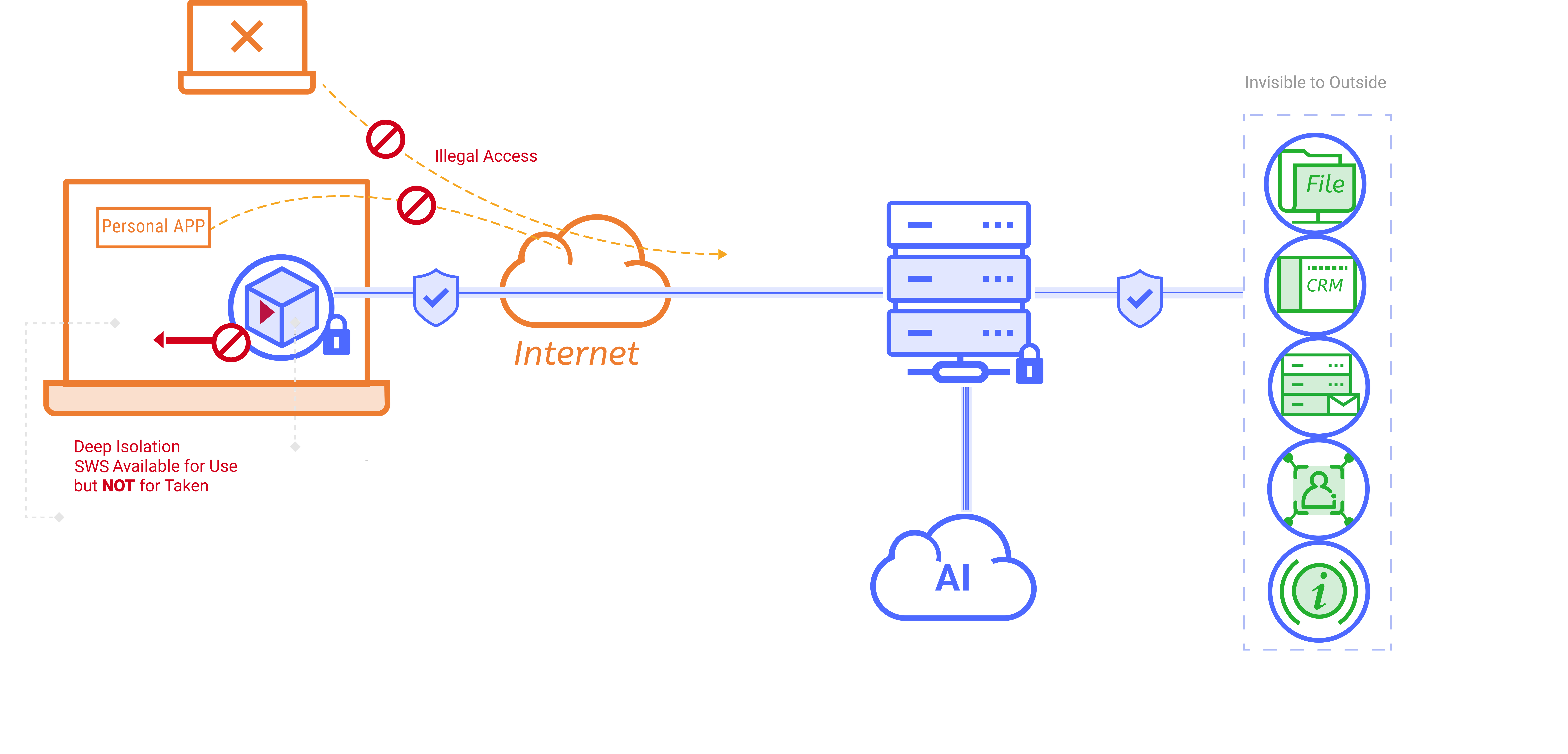
- Adhering to the core idea that "defense mechanisms are built following the flow of data", defense mechanisms are constructed wherever the data flows, providing refined and close-fitting protection measures for data services.
- Using new - generation security sandboxes (micro - kernels, secure containers, trusted computing), high - performance network tunnels, software - defined perimeters, AI - based security policy engines and other technologies, it realizes precise access control and effective isolation and management of sensitive data, builds an enterprise terminal data adaptive security management and control platform and solution. Under the premise of ensuring security, it meets the diverse needs such as full data flow, full data sharing, and mobile office scenarios, and maximally guarantees enterprise data security, enabling new businesses of enterprises in the digital transformation era.
Dataillusion ZTNA™ (Zero Trust Network Access)
- A network access control system launched based on the zero - trust framework, following the concepts of "trusted identity, trusted access, intelligent permissions, and minimal maintenance", it builds a dynamic access perimeter for users to eliminate excessive implicit trust. It realizes trusted identity, trusted devices, trusted environments, and trusted links in the remote work scenario, helping enterprises continuously evolve their security capabilities.
Dataillusion DCR™ (Data Clean Room)
- A network access control system launched based on the zero - trust framework, following the concepts of "trusted identity, trusted access, intelligent permissions, and minimal maintenance", it builds a dynamic access perimeter for users to eliminate excessive implicit trust. It realizes trusted identity, trusted devices, trusted environments, and trusted links in the remote work scenario, helping enterprises continuously evolve their security capabilities.